The 45-Second Trick For File Migration To Sharepoint
At the bottom of the web page, choose. Under, select: Leave these setups in location for the duration of your movement.
Proxy links are not supported for either Share, Factor or data share migrations. Instances of mistakes you might see consist of "Share, Point login stop working" or "can not load record collection".
If you want to utilize your system proxy settings, make use of one of these methods: Download and install the latest version of SPMT. Open up the file. If SPMT can not update itself, go to Open up the file.
Open the data. Comment out the default proxy setting: Reactivate SPMT. file migration to sharepoint. Keep in mind Currently, the is not available for individuals of Workplace 365 operated by 21Vianet in China.
Not known Factual Statements About File Migration To Sharepoint
This guide helps you prepare to migrate from documents shares to One, Drive, Groups, and also Share, Factor in Microsoft 365. Keep in mind Moving your data shares with Migration Manager lets you have a centralized means of attaching web servers, developing jobs, and also immediately tons balancing your migration jobs.
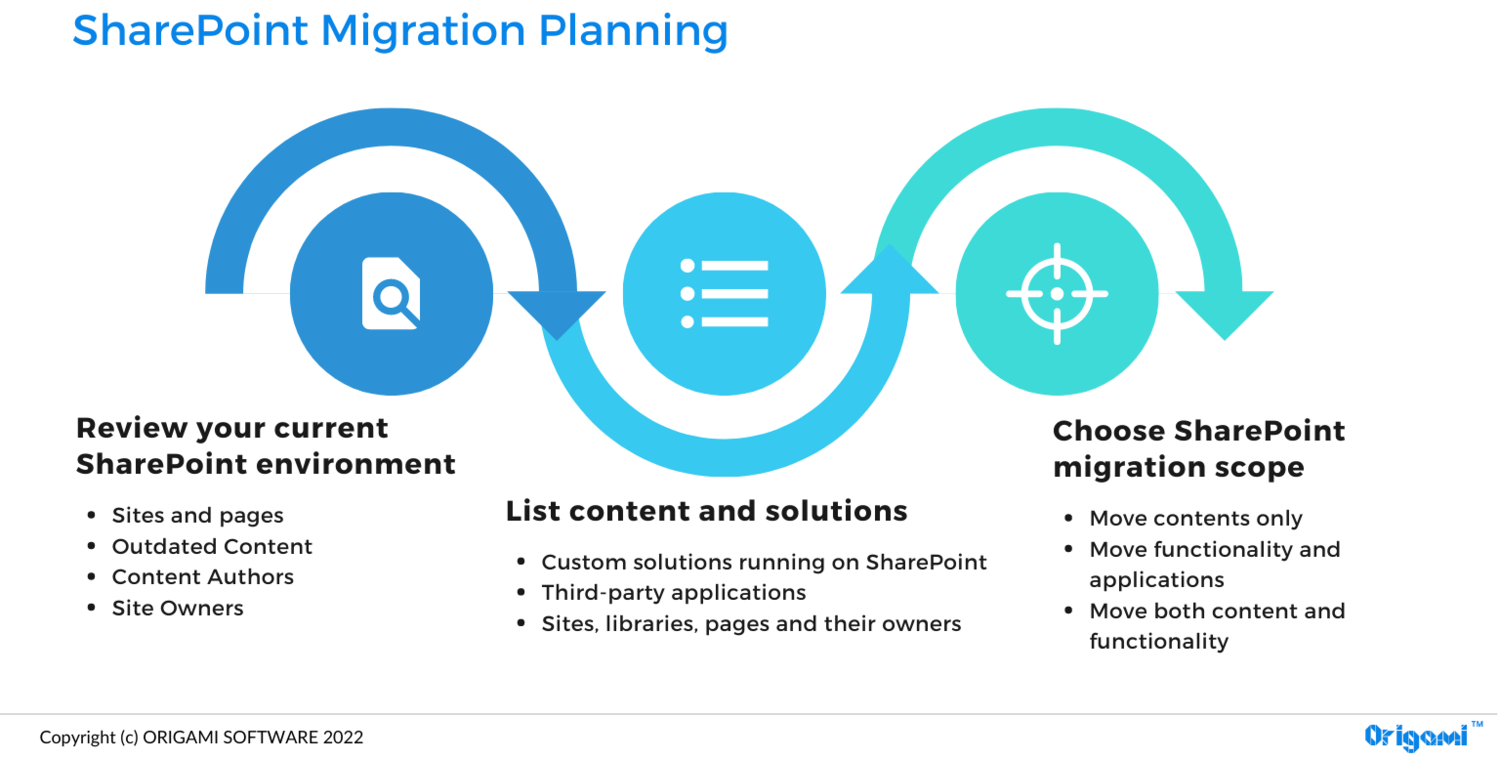
Movement planning Assess and remediate Prepare your One, Drive and also Share, Point setting Migrate Customer onboarding What web content goes where, Recognizing approvals vs sharing, What to anticipate before as well as after, Migration and also network performance considerations, Adjustment management and also interactions Evaluate key locations, Remediate issues Pre-provision Microsoft 365 and also individuals Review movement offerings, Microsoft Quick, Track services, Movement company Send out routine emails to customers, Give training, Let users understand exactly how they are impacted Documents shares include systematized data hosting on a network web server or a network drive or shared data or disks on a local computer system.
Before you begin your migration, it is necessary that you prepare your outcome by doing an evaluation of your current source setting. What you discover will certainly affect your total approach as well as timing, including: The layout of the target environment and the mapping between source and also target systems. The amount of content you move.
Build your individual onboarding right into your upfront preparation. Communicate early as well as frequently with your customers about the movement and how it will influence them. Do not wait until the actual end to begin preparing them for the change. When getting ready for your documents share movement, it's vital to understand what's being moved when you make use of the Share, Factor Movement Tool as well as what's not - file migration to sharepoint.
The Ultimate Guide To File Migration To Sharepoint
Does the documents belong to a solitary individual, even though they might share it with others? Your One, Drive is exclusive by default, however you can share files with others, which is specifically valuable if you aren't working as a group.
One, Drive provides you accessibility to all your shared collections in Microsoft Teams, Share, Factor, or Overview. When you require a new common library for team files, you can develop one right from One, Drive, add participants, as well as begin interacting. Just how you have shared your documents dictates just how they appear in the sight in One, Drive.
A customer's folder in One, Drive won't be upgraded for source documents shown a team the user belongs of. After migration, all progressed NTFS approvals are eliminated. For specific refute authorizations, this means the web content goes through parallel approvals or approval on the folder and moms and dad degree and may come to be obtainable.
The Share, Factor Movement Device (SPMT) provides the capability to check your documents and also provide assessment records. To discover any kind of issues with your data before migration, turn on the setting. If the obstructed documents kinds are scripting documents, they are obstructed due to the fact that scripting capabilities are turned off by default in One, Drive.
Ensure you comprehend why these data are obstructed by default Recommended Reading as defined below: Safety and security considerations of enabling personalized script. Locate all products in the Folders as well as Data report whose name consists of any of the personalities detailed below: Void file names as well as data key ins One, Drive and Share, Point Work with your migration vendor to replace these personalities in all data as well as folder names.
Comply with these actions to enable them: New support for # and % in Share, Factor and also One, Drive. Locate all products in the Folders as well as Files report whose Course goes beyond the documents course length defined below: Share, Point limits Collaborate with your movement supplier to rearrange your file and also folder framework such that it does not exceed this limit.
Prior to you move your file share content, you must try this website pre-provision your customers in Microsoft 365. For support on pre-provisioning, see The click site following is a common migration procedure that complies with Microsoft's finest practices advice. Essential Make sure that the account utilized to move material has authorizations on the destination One, Drive.